|
|
|
|
|
| Friday 29 January 2010
|
|
|
|

|
Security Jam Navigation Toolbar |
|
AFGHANISTAN ■ CRISIS MANAGEMENT ■ CLIMATE CHANGE
COMPREHENSIVE APPROACH ■ HUMAN RIGHTS
CAPABILITIES & TRAINING ■ DEVELOPMENT
RELATIONS WITH RUSSIA & CHINA
PIRACY ■ SECURITY |
|
The Security Jam will take place in ten interactive Discussion Forums moderated in real-time by leading experts in their field who will act as online Hosts over the five day event.
Each Discussion Forum is centred on a key security issue.
1. Political Context
“What do we understand by security?”
How many of the security threats of the 20th century are still valid in the 21st century? How should governments view new non-state threats like terrorism, piracy, nuclear proliferation, energy disruptions and climate change?
2. Capabilities & Budgets
“Will the tools of today be suited to the missions of tomorrow?”
Today’s security challenges require a diverse toolbox ranging from complex weapons systems to the most basic elements of civil protection and disaster relief. How ruthless should we be in scrapping systems and equipment that was designed for 20th century defence scenarios? How should we train and equip ourselves to cover an ever-growing range of operations? How can the financial burden be more equally shared amongst stakeholders?
3. Crisis Preparedness
“How can we prepare for the unexpected?”
Re-allocating resources to prevention and early action could save billions of euros while reinforcing cooperation with NGOs on the ground. What should be done to streamline approaches to crisis management? How can we more intelligently allocate resources and train personnel? How can we better coordinate between the wide ranges of players – from military to civilian – involved?
4. Development
“How can we balance development, security and diplomacy?”
How do civilian development experts – not least the NGOs with “frontline” responsibilities – see the difficulties of combining security and crisis management questions with longer-term development tasks? What steps are needed to further improve close working relationships between NGOs and the military? Do NGOs have a loud enough voice on security policymaking?
5. Security and Human Rights
“How do we reinforce civil society efforts”
The increasingly complex threat from terrorism puts enormous pressure on states to protect their citizens through operations at home and abroad. But how do we justify humanitarian intervention when basic human rights and freedoms can be jeopardized? How can we better work with civil society to make sure we do not aggravate the root causes of terrorism and non-state actor violence?
6. Environmental Security
“How can we balance security and climate change?”
Future conflict will increasingly be sparked by environmental factors, as the struggle for scarce resources grows ever more acute. Given that nature does not respect the boundaries of politics or time, diplomats and policy makers must ensure long-term solutions that involve civil society.
7. Comprehensive Approach
“How coordinated can our response to global threats be?”
Western forces will increasingly be called upon to support world-wide peace and bring order to societies under strain. There have been recent calls for increased cooperation and collaboration between the world’s major security actors (the UN, the EU, NATO, the AU, OSCE, etc). How should this be implemented in practice?
8. Rising Powers
“How should we adapt Western security thinking to the rise of Russia, China and India?”
China and Russia are widely seen as rising counter-balances to Western military power. That poses fundamental questions as to how Western strategic thinking towards the two should develop, as well as prospects for future cooperation.
9. Case Study I: Piracy
“How do we learn from the Gulf of Aden?”
By January 2009, an estimated thirty ships with staff from more than a dozen countries were patrolling an area of approx. 2.5 million square miles. If any current operation provides an opportunity for international actors to discuss common approaches, lessons learned and future challenges, this is it.
10. Case Study II: Afghanistan
“If we could start over in Afghanistan, how would it be done?”
Few expected stabilization to still be Afghanistan’s major challenge eight years later. What are the lessons learned from how we entered eight years ago? What mistakes should be avoided? If you were given a blank page on the next such intervention, what would you do differently?
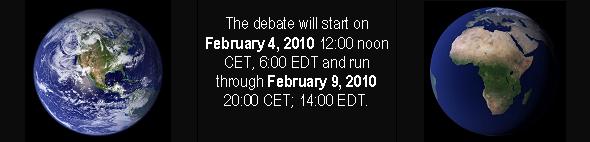
Click here to register your voice for the 2010 Security Jam
 |
|
|
|
|
|
|
| Login | Powered by IT Omni CMS |